The CrowdStrike Falcon Sensor Outage: Preparing for the Unexpected
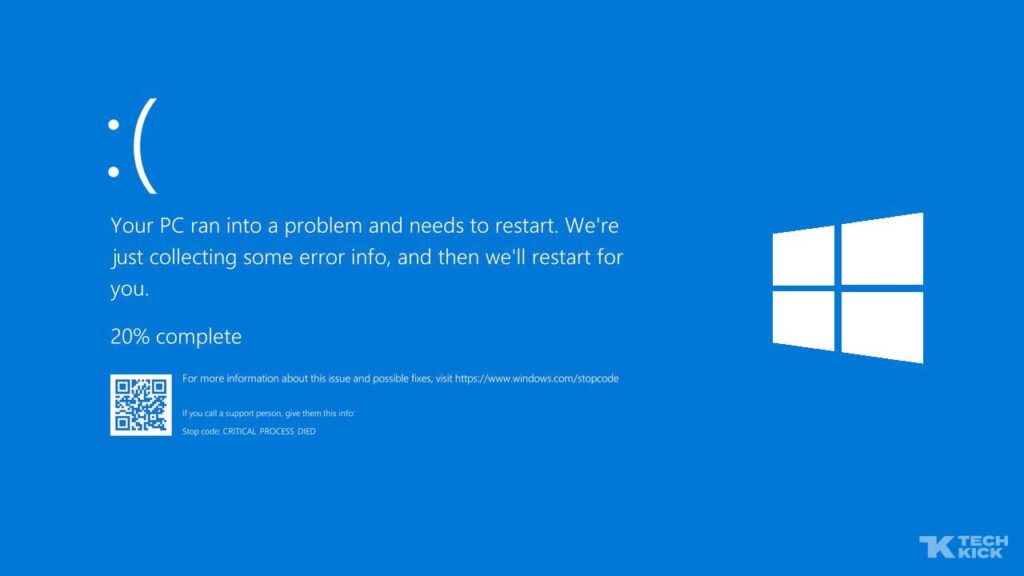
If you ever wondered what a cyber apocalypse would look like, the recent CrowdStrike Falcon Sensor outage might’ve given you a glimpse. Categorized as a software defect and not a malicious cyberattack, the IT outage involving CrowdStrike’s Falcon Sensor software was caused by a defect in a content update specifically affecting Windows hosts. This led […]
Understanding Smishing Attacks

Ever gotten a “STOP” to unsubscribe text? That may have been smishing bait to identify active phone numbers. Smishing (SMS + phishing) is a common cybersecurity threat in which attackers use text messages to trick people into disclosing sensitive information. This attack exploits our mobile habits, luring us into trusting seemingly familiar numbers amidst the […]
Addressing Today’s Cyber Challenges: The Ultimate Solution

In today’s digital age, cybersecurity has become a paramount concern for businesses and organizations of all sizes. With cyber threats evolving in complexity and frequency, safeguarding sensitive data and systems has never been more critical. In this blog, we’ll explore common cybersecurity threats and some powerful tools from industry giants to enhance your company’s security posture.
Navigating the Cybersecurity Landscape: A Starter Kit

This blog equips you with news, careers and salary insights for staying informed and advancing in the field of cybersecurity.
